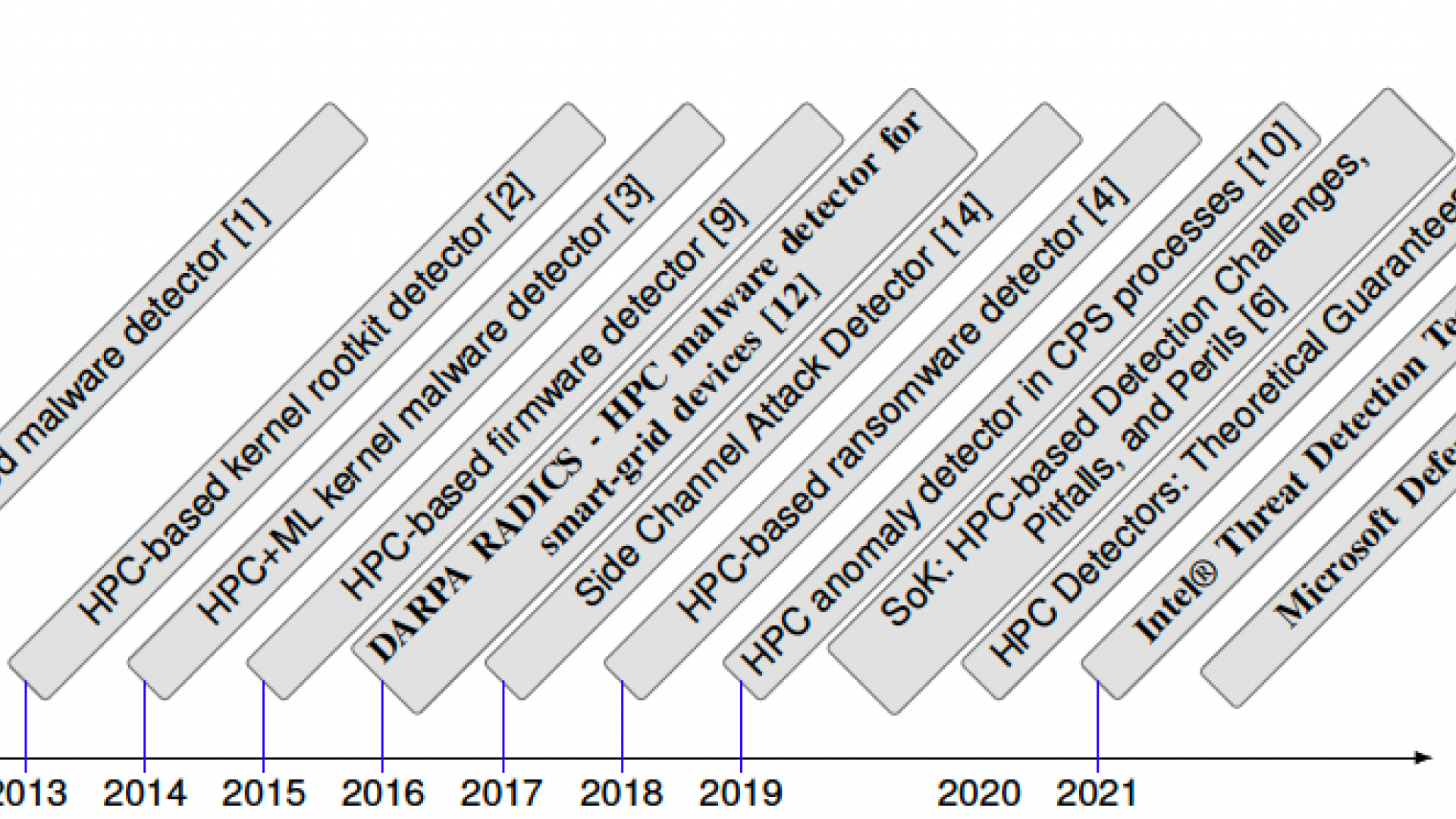
HPC-based Malware Detectors Actually Work: Transition to Practice After a Decade of Research: Our recent work has come out as the result of our research on HPC (hardware performance counters) security in the last decade. During this time, HPC-based malware detection transitioned from academic research through government transition to industry adoption. In this paper, we outline this evolution by presenting use cases on critical power grid infrastructure protection as part of DARPA RADICS program, as well as describing how HPCs are utilized within Intel’s HPC-based Threat Detection Technology (TDT), which is further used by Microsoft Defender for Endpoint. We also highlight our 2015 ICCAD work, selected as Top Pick in Hardware and Embedded Security 2020 (most influential papers for 2012-2017), on HPC-based malware detection to detect firmware modifications in embedded systems.
Postprint available: KAUST Repository & IEEEXplore