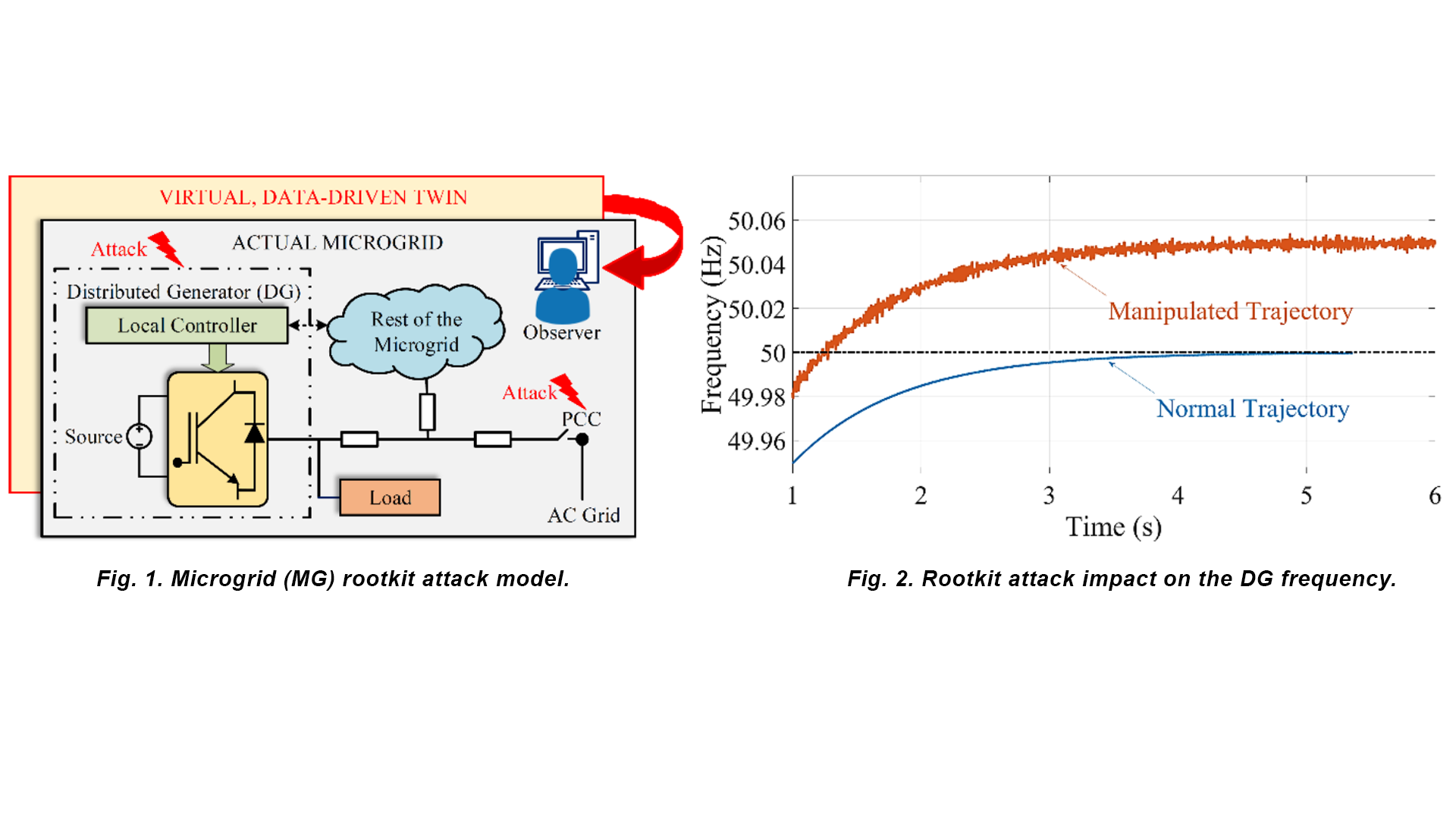
2022 IEEE Power & Energy Society General Meeting Conference (PESGM) authored by Suman Rath, Ioannis Zografopoulos, Pedro P. Vergara, Vassilis C. Nikolaidis, Charalambos Konstantinou
“Embedded controllers, sensors, actuators, advanced metering infrastructure, etc. are cornerstone components of cyber-physical energy systems such as microgrids. Harnessing their monitoring and control functionalities, sophisticated schemes can be employed to improve power system operations. However, the deployment of ‘smart’ assets increases the threat surface of the power grid. Power systems possess mechanisms capable of detecting abnormal operations, and the lack of sophistication of certain attacks renders them detectable since they blindly violate the power system semantics. On the other hand, the recent increase of process-aware rootkits, which can attain persistence and compromise operations in undetectable ways, requires special attention.
Rootkits represent a class of malware which can intelligently hide their presence inside their targets. During the system information aggregation phase, rootkits eavesdrop system data and allow attackers to collect real-time system information via remotely accessible connections. Then, during the weaponization stage, adversaries can exploit these connections to issue malicious commands, manipulate the infected device(s), and stealthily control their operation. Rootkits use different approaches to conceal their presence and disguise the impacts of attacks, overcoming existing security fortifications exploiting system state estimations.
Microgrid-based process level rootkit attacks should be considered when designing and implementing detection and mitigation strategies and should represent a crucial part of reliability assessment procedures. To thwart rootkit attacks, it is crucial to identify and eliminate vulnerabilities in embedded control devices and understand the operational objectives and potential impacts of such attacks.
In this work, we investigate the steps followed by stealthy rootkits at the process level of control systems pre- and post-compromise. We examine the rootkits’ pre-compromise stage involving the deployment to multiple system locations and aggregation of system-specific information to build a neural network-based virtual data-driven model (VDDM) of the system (Fig. 1). Then, during the weaponization phase, we demonstrate how the VDDM measurement predictions are paramount, first, to orchestrate crippling attacks from multiple system standpoints (maximizing the attack impact), and second, to impede detection inhibiting the system operator situational awareness. We demonstrate the achievable system impacts via simulations performed on our real-time cyber-physical testbed infrastructure (Fig. 2).